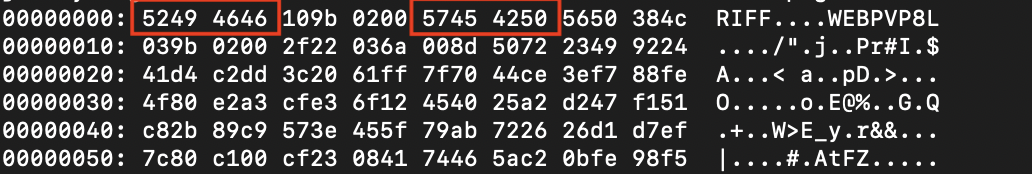
The Magic Byte
TLDR: Novice learn about magic bytes for the first time and learn about the importance of understanding the mechanism behind implementations Thursday Night, an image file upload vulnerability in an attack box. I had a linear plan. Fuzz the file extension and use whatever got through for command injection. Reality hit me as I soon found out it was not so simple. My SVG XXE payload got through, but I could not say the same for my PHP payload. So, I use XXE to peek into the file type mechanism. ...